IP VPN Technology
The technology known as a Virtual Private Network (VPN) is used to establish private networks over public network infrastructure, including the worldwide Internet. By encrypting packets to ensure a secret conversation and verifying the endpoints’ identities, a VPN’s primary purpose is to protect communication between two devices.
VPNs typically use virtual connections called VPN tunnels that are sent from a private network to a distant location or employee host across the public network. Secure access to remote resources is made possible by using a virtual private network (VPN), which makes a local host appear to be local on the distant network.
Core Security Features and Benefits of VPNs
Strong security measures are offered by VPNs, especially when using the unprotected public Internet:
| Security Feature | Description |
|---|---|
| Confidentiality (Privacy) | Prevents anyone (e.g., a man-in-the-middle attacker) from reading the data by using encryption. This is the primary goal of confidentiality. |
| Data Integrity | Verifies that the packet was not changed as it transited the Internet. |
| Authentication | Verifies that the sender of the VPN packet is a legitimate device and not an attacker. |
| Anti-replay | Prevents an attacker from copying and later replaying packets sent by a legitimate user. |
When opposed to costly dedicated WAN links, the benefits of deploying a virtual private network (VPN) service are significant:
- Cost savings: Businesses can save a significant amount of money by establishing an encrypted VPN tunnel and linking corporate remote offices to their nearest Internet provider, as opposed to using conventional leased point-to-point lines.
- Scalability: VPNs are incredibly scalable, enabling the rapid addition of large volumes of capacity without requiring any adjustments to the infrastructure, safely accommodating new offices or mobile customers.
- Broadband compatibility: Telecommuters and mobile workers can safely access company networks by using their high-speed home Internet services (cable or DSL).
Types of VPN Access
Generally, VPNs are divided into groups according to the function they provide, such as provider-managed or enterprise-managed solutions. Site-to-site, extranet, and remote access VPNs are the three primary varieties.
Also Read About Man In The Middle MitM Phishing Attacks And How It Works?
Remote-Access VPNs (Client VPNs)
This kind makes it possible for individual hosts like telecommuters, mobile users, or extranet consumers to safely access a business network via the Internet.
- Endpoint: One endpoint is the user’s device, such as a PC, tablet, or phone.
- Common Use: Usually, the connections are made as needed.
- Protocols: To establish a secure VPN session, remote access VPNs typically employ the Transport Layer Security (TLS) protocol, which is an SSL substitute.
- Client Software: In order to establish a complete TLS tunnel that encrypts all traffic going to the corporate network, software such as the Cisco AnyConnect Secure Mobility Client must be installed on the host. This allows for client-based remote access. As an alternative, clientless VPN connections also known as clientless Secure Sockets Layer/SSL connections can be made using web browsers. These connections are frequently excellent when restricted access from a borrowed device is required.
Site-to-Site VPNs
Site-to-site virtual private networks (VPNs) link entire networks together, such a branch office network to the corporate headquarters network.
- Endpoint: To establish a single permanent VPN tunnel that supports numerous devices at the site, network engineers configure a VPN gateway (router, firewall, VPN concentrator, or security appliance) at each location.
- Common Use: Usually, the tunnels are left intact and run continuously.
- Protocols: IPsec is commonly used as the security protocol in site-to-site virtual private networks.
Types
Extranet VPNs
For business-to-business (B2B) interactions, these VPNs connect external parties like clients, partners, or suppliers to a company intranet.
Intranet VPNs
One kind of site-to-site VPN is an intranet VPN, which uses the public internet as a communication channel to safely link several offices or branches of the same company.
It makes it possible for workers in various places to access corporate resources as if they were all linked to the same local area network (LAN).
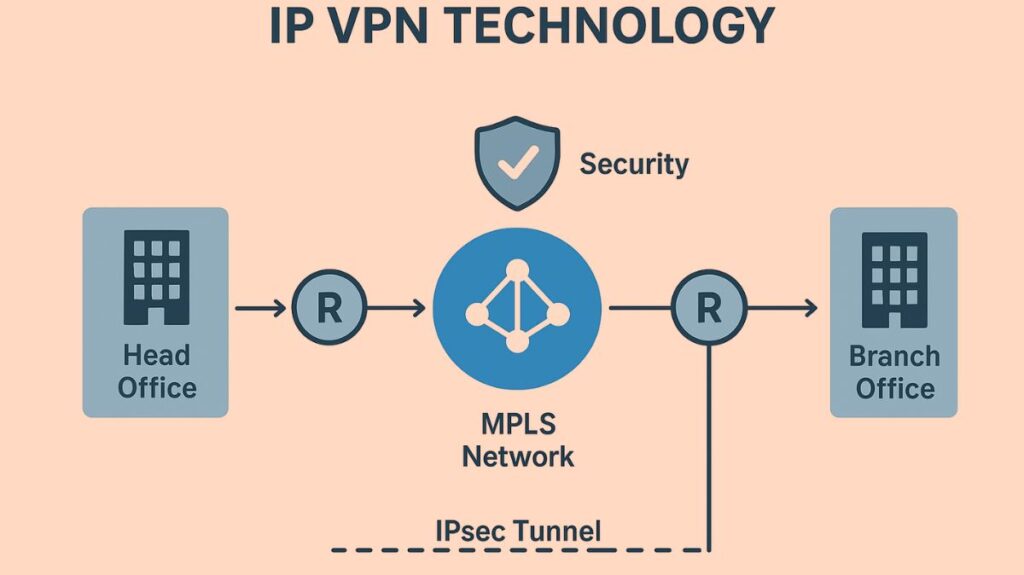
Provider-Managed MPLS VPNs
These services, which are run by a service provider (SP), transfer data between client sites using MPLS labels:
- Layer 3 MPLS VPN: Each customer site is connected via a separate IP subnet, and the SP takes part in customer routing.
- Layer 2 MPLS VPN: The SP simulates an Ethernet multiaccess LAN segment over the MPLS network by using services like Virtual Private LAN Service (VPLS) or Virtual Private Wire Service (VPWS), but it does not take part in customer routing.
VPN Protocols and Technologies
Internet Protocol Security, or IPsec, is a widely used industry standard framework that functions at the OSI model’s Layer 3 Network layer. It serves as the basis for safe site-to-site virtual private networks.
- Using symmetric encryption techniques, such Triple DES (3DES) or Advanced Encryption Standard (AES), which are quicker than asymmetric ones, confidentiality is achieved. The Encapsulating Security Payload (ESP) protocol is the particular protocol that IPsec uses to encrypt data packets.
- Integrity and Authentication: Hashing algorithms, such as SHA or MD5, are used to verify integrity. Authentication is usually done with digital signatures or pre-shared keys (PSKs) close to the start of the session.
- Key Exchange: To safely exchange encryption keys, VPN peers create a Security Association (SA) using the Internet Key Exchange (IKE) protocol.
Generic Routing Encapsulation (GRE)
GRE is a proprietary Cisco tunnelling technology that creates virtual point-to-point links that may encapsulate a variety of protocols inside IP tunnels, including multicast/broadcast traffic and routing protocols like OSPF or EIGRP.
- Because GRE does not allow encryption by default, it is not secure.
- GRE is frequently encapsulated within IPsec (GRE over IPsec) to produce a secure tunnel capable of carrying multicast traffic.
Dynamic Multipoint VPN (DMVPN)
A Cisco proprietary solution called DMVPN makes it possible to create expansive, dynamic, and scalable IPsec VPNs.
- Topology: To create a complete mesh topology, DMVPN employs a hub-and-spoke arrangement.
- Functionality: It uses Next Hop Resolution Protocol (NHRP) and Multipoint Generic Routing Encapsulation (mGRE) to simplify configuration and dynamically create hub-to-spoke and spoke-to-spoke tunnels.
IPsec Virtual Tunnel Interface (VTI)
A Cisco proprietary configuration method called IPsec VTI makes it easier to set up a VPN for remote access and allows IP unicast and multicast encrypted traffic to be sent and received without the need for separate GRE tunnels.
VPN Components
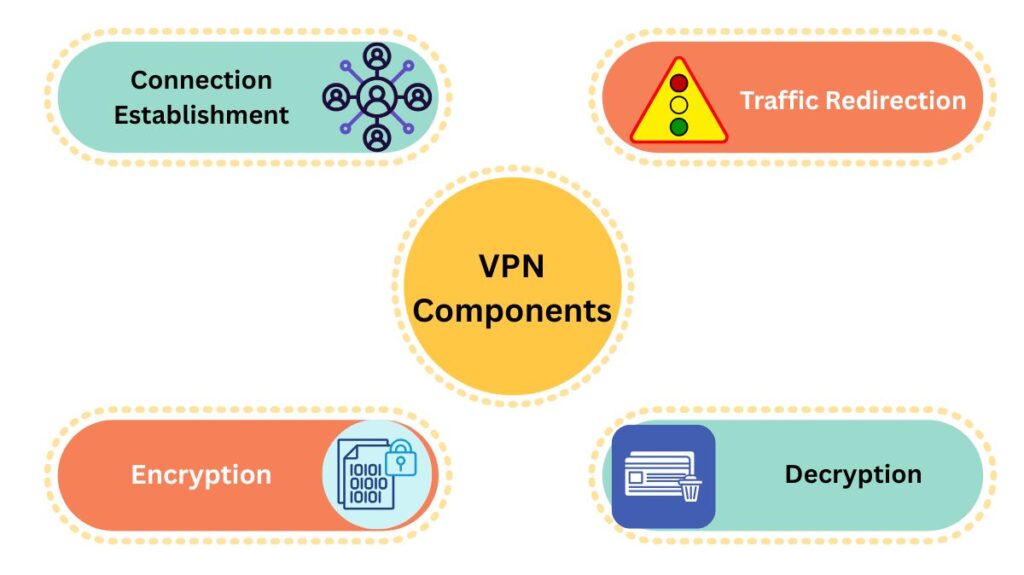
The following essential elements are needed to create a standard VPN topology:
- Connection Establishment: Your device establishes a connection to a server run by the VPN provider when you turn on a VPN.
- Encryption: Whether it’s a hacker on the same Wi-Fi network or an organisation attempting to track your browsing, the VPN encrypts your data (files, information, and web traffic) to make it unintelligible to anyone attempting to intercept it.
- Traffic Redirection: The VPN server, which may be situated in any nation, routes the internet traffic coming from your device. This hides your true IP address and gives the impression that you are browsing from the server’s location.
- Decryption: Your data is decrypted and delivered to the destination (such a website, app, or service) after it has arrived at the VPN server. You then receive any answer from the server via the encrypted tunnel.
VPN Tunneling (Encapsulation)
This method uses a common infrastructure to transfer data transparently from the source network to the destination network. Three sorts of protocols are used in tunnelling:
- The original data protocol being encapsulated, such as IPv4, IPv6, IPX, or AppleTalk, is known as the passenger protocol.
- Encapsulating Protocol: The protocol (such as GRE, IPsec, L2F, PPTP, or L2TP) that encloses the original data.
- Carrier Protocol: The protocol (such as IP, Frame Relay, PPP, or MPLS) that the entire system moves over.
VPNs in Cloud Architecture
To create secure connectivity between a public cloud provider and a business network, virtual private networks, or VPNs, are widely utilized.
The company can use its own router to set up a VPN tunnel to the cloud, or it can use a virtual router (VM) within the network of the cloud provider, like the Cisco Cloud Services Router (CSR), to set up and stop VPN services. In this case, using an Internet VPN greatly improves security over an unencrypted Internet connection by encrypting the data to preserve anonymity.
