IPsec VTI
A Cisco-proprietary method of configuring IPsec that makes setting up Virtual Private Networks (VPNs) much easier is the IPsec Virtual Tunnel Interface (VTI). It symbolizes a contemporary transition from route-based IPsec to traditional policy-based IPsec, which depends on crypto maps and Access Control Lists, or ACLs.
Core Mechanism and Operation
On a network device, IPsec VTI establishes a logical, routable tunnel interface:
- Virtual Interface Creation: A VTI establishes a routable virtual interface (such as
Tunnel 0) on the router or firewall, functioning much like a physical interface.
- Route-Based Traffic Selection: The main distinction with traditional IPsec is route-based traffic selection. VTI uses the IP routing table to define “interesting traffic” that needs to be encrypted, rather than intricate ACLs or crypto maps. All traffic going to the distant location is directed in the direction of the virtual tunnel interface.
- Encryption: Before sending traffic out of the physical interface, the router immediately encrypts it using the configured IPsec profile after it has been forwarded to the VTI. IPsec VTI ensures confidentiality by encrypting every traffic it handles.
- Encapsulation: To guarantee delivery to certain locations, IPsec VTI tunnels encapsulate traffic with new packet headers and offer a dedicated path across a shared Wide Area Network (WAN).
A common configuration for a route-based setup involves defining the local and remote networks simply as 0.0.0.0/0, meaning that anything with a route pointing to the VTI can travel through the tunnel.
Key Benefits and Capabilities
Compared to older IPsec implementations, the VTI mode improves functionality and streamlines management:
- Configuration Simplification: By reducing the requirement for local IT help, VTI significantly reduces the complexity of VPN configuration, which lowers expenses. Compared to utilizing ACLs with crypto maps, employing IP routing to forward traffic makes configuration simpler.
- Dynamic Routing Support: The VTI supports all IP routing protocols (including RIP, OSPF, EIGRP, and BGP) directly across the tunnel since it is a routable interface. This enables remote sites to advertise subnets via the secure connection and learn them dynamically.
- Multicast and Unicast Traffic: IP unicast and multicast encrypted traffic can be handled by VTI. Routing protocols are automatically supported because they support multicast, eliminating the need to configure individual Generic Routing Encapsulation (GRE) tunnels and the related overhead.
- Scaling: By requiring fewer established security associations to support various traffic types (unicast and multicast), VTI enhances scaling. It is quite scalable for VPNs with partial or complicated meshes. A significant difficulty for ageing systems, the method reduces the complexity and resource load of continuously updating crypto ACLs whenever networks are added or withdrawn.
- Flexibility and Features: VTI has features that can be defined to operate on the IPsec or physical interface. VTI can be used with rich services like Zone-Based Firewall (ZBFW), Virtual Routing and Forwarding (VRF), Network Address Translation (NAT), and Quality of Service (QoS).
Types of IPsec VTI
There are two primary varieties of VTI, which are primarily utilized in hub-and-spoke or site-to-site settings:
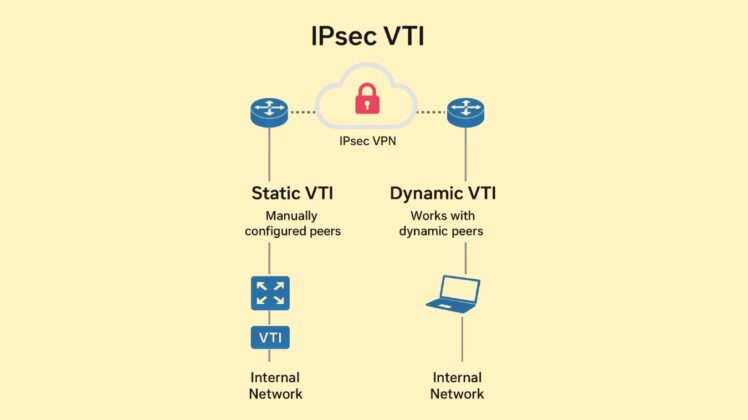
Static Virtual Tunnel Interface (SVTI)
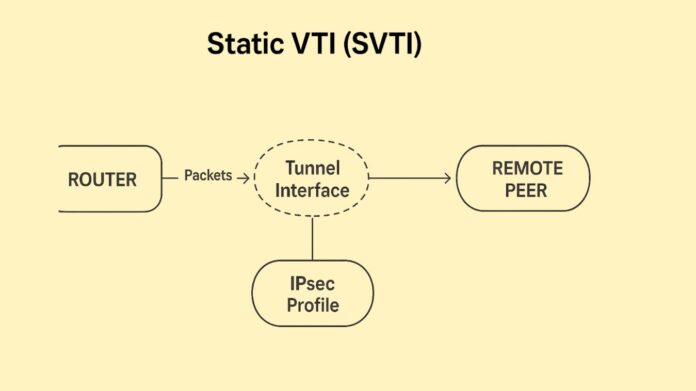
when the peers in a site-to-site VPN have fixed IP addresses. On the VTI, the tunnel’s source and destination IP addresses are manually set up and static.
In order to set up IPsec VPN tunnels, Cisco routers and firewalls mostly use a feature called a Static Virtual Tunnel Interface (SVTI). Employing a virtual interface as the VPN’s termination point instead of implementing the IPsec configuration directly on a physical interface streamlines the IPsec setup process.
Key Characteristics and Functionality
- Virtual Interface: By constructing a logical tunnel interface, SVTI functions similarly to a point-to-point connection. This interface has an IP address set up, and for routing purposes, the router handles it just like any other physical interface.
- Routing Integration: SVTI’s primary benefit is its smooth integration with dynamic routing protocols, such as OSPF, EIGRP, or BGP. Compared to static route-based VPNs, the network topology is more scalable and manageable since the router may easily advertise the routes it has learnt via the virtual interface.
- Simplicity of IPsec: SVTI employs a Tunnel Protection Profile in place of intricate Crypto Maps, which are more antiquated and laborious. The virtual interface is tied to the IPsec settings (such as IKE/IPsec policies and encryption/hashing methods).
- Mode of Operation: IPsec Tunnel Mode is the main mode of operation for SVTI. This adds a new IP header and encrypts the entire original IP message.
You can also read Cisco Dynamic Multipoint VPN DMVPN Phase 1 2 3 In Network
Dynamic Virtual Tunnel Interface (DVTI)
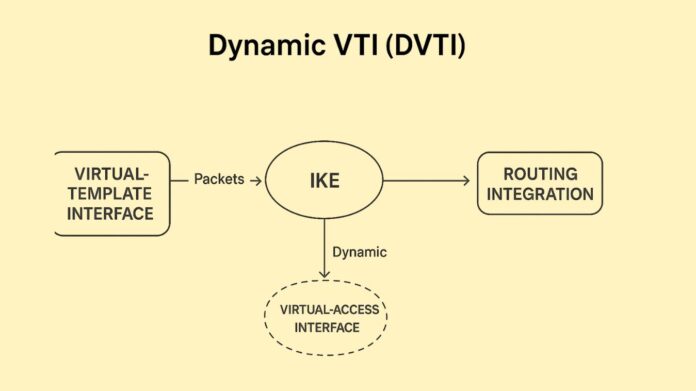
A Cisco feature called Dynamic Virtual Tunnel Interface (DVTI) generates a transient, on-demand virtual interface for an IPsec VPN tunnel. It is frequently utilized with Dynamic Multipoint VPN (DMVPN) or remote-access solutions.
A DVTI is only produced when a remote peer tries to establish an IPsec connection, and it is destroyed at the end of the session, in contrast to Static VTI (SVTI), where the tunnel interface is permanently established for a particular peer.
Key Characteristics and Functionality
- On-Demand Creation: DVTI interfaces are not set up permanently. Every time a new VPN peer authenticates, they are dynamically instantiated (cloned) from a single template interface.
- Remote Access/Hub-and-Spoke: DVTI is the industry standard for constructing spoke-side configurations in DMVPN networks or remote-access VPNs (such as Cisco AnyConnect). A hub in DMVPN can receive connections from several spokes, each of which is given a dynamic VTI, by employing a static interface.
- IPsec Integration: The DVTI setup links the IPsec policy, which is specified by a tunnel protection profile, directly to the virtual interface, much like SVTI does. This takes the role of more intricate, earlier techniques like Crypto Maps.
- Routing Support: Since the dynamically generated DVTI is a virtual interface, it may take part in dynamic routing protocols (such as OSPF or EIGRP), which enables routes to be automatically learnt and advertised as tunnels appear.
How DVTI Works (in a DMVPN Context)
- Tear Down: The dynamic DVTI is eliminated to free up resources when the spoke disconnects or the security association expires.
- Peer Authentication: Peer authentication is the process by which a distant VPN router (spoke) tries to establish a connection with the hub, the central VPN router.
- IPsec/IKE Phase 1 & 2: The hub creates the IKE Security Association (SA) and subsequently the IPsec SA by authenticating the spoke using its pre-shared key or digital certificate.
- DVTI Instantiation: The hub creates a distinct, transient virtual interface for that particular spoke by copying the DVTI template configuration after authentication is successful.
- Traffic Forwarding: This interface, which is secured by the agreed-upon IPsec SAs, is used to forward traffic to the spoke after this new DVTI is given a tunnel IP address.
One of the technologies used by Cisco’s Dynamic Multipoint VPN (DMVPN) solution is VTI, which makes it simple, dynamic, and scalable to construct several VPNs.
Similar to regular IPsec, VTI usually only supports one protocol (either IPv4 or IPv6); however, for real dual-stack support, specialized modes such as FlexVPN are advised.
You can also read Types And Advantages Of Intrusion Prevention System IPS
