In this article, we learn about what Kerberos is, Purpose of Kerberos, Components of Kerberos, and Limitations of Kerberos
Kerberos
A complex computer network authentication system called Kerberos was created to give client-server apps running over insecure networks, like the internet, strong authentication.
Kerberos, which was created in 1988 by the Massachusetts Institute of Technology (MIT) to safeguard network services for Project Athena, is a time-stamped ticket-based system that enables interacting nodes to safely verify their identity.
The fierce three-headed guard dog of Hades in Greek mythology, Kerberos (or Cerberus), is the inspiration behind the protocol’s name, metaphorically signifying its three main elements.
You can also read What is Diameter protocol Explained, Applications & Commands
What is the Purpose of Kerberos?
Network security problems can be solved with Kerberos, especially when credentials could otherwise be “sniffed” (eavesdropped) via the network.
- Ticket-Based System: Kerberos uses brief, encrypted tickets for identity verification in place of frequently delivering passwords. The network is never used to send passwords.
- Mutual Authentication: Before a session starts, the user (client) and the service (server) confirm each other’s identities Kerberos’ mutual authentication feature.
- Single Sign-On (SSO): One important advantage is Single Sign-On (SSO), which allows a user to authenticate once at the start of a session and then access different network resources without having to provide their login information again for each service.
- Cryptography: Although it can choose to employ public-key cryptography at specific stages of authentication, Kerberos mostly relies on symmetric-key cryptography, also known as secret-key cryptography. Messages sent using the Kerberos protocol are shielded from replay and eavesdropping attempts.
Components of Kerberos
Three primary entities are involved in the Kerberos protocol:
- Client/User (The Principal): The person or device requesting access to a resource is known as the client or user (the principal).
- Server/Service (SS or Application Server): The client’s desired application or resource is the server/service (SS or Application Server).
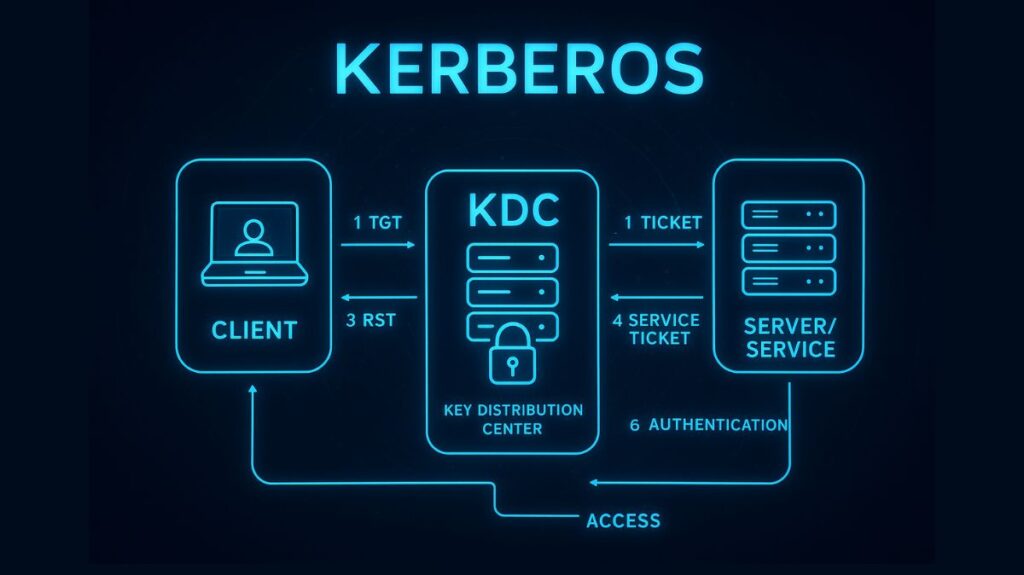
- Key Distribution Center (KDC): This is the reliable third party that issues tickets and keeps track of the secret keys. It makes sense to divide the KDC into two sections:
- Authentication Server (AS): The Ticket-Granting Ticket (TGT) is issued by the Authentication Server (AS), which also handles the initial client authentication.
- Ticket Granting Server (TGS): Issues a Service Ticket (ST) for a particular application server after authenticating customers using the TGT.
You can also read What is PEAP Protected Extensible Authentication Protocol?
Simplified Protocol Flow (The Ticket Exchange)
The TGT and the Service Ticket are the two main ticket kinds that are securely exchanged throughout the entire process.
- Initial Authentication (Client to AS): The client requests a TGT from the Authentication Server (AS) in plaintext using the user ID. The user is validated by the AS using its database.
- TGT Issued (AS to Client): If the user is located, the AS generates the user’s secret key (by hashing the password) and sends back two messages: the Client/TGS Session Key encrypted with the user’s secret key and the Ticket-Granting Ticket (TGT), which is encrypted with the TGS’s secret key to prevent the client from reading it. The client decrypts the session key using the password that was entered locally.
- Service Ticket Request (Client to TGS): The client transmits the encrypted TGT (Message B/C) and an Authenticator (encrypted using the Client/TGS Session Key) to the Ticket-Granting Service (TGS) in order to access a particular network service.
- Service Ticket Issued (TGS to Client): The TGS creates a Service Ticket (ST) and a new Client/Server Session Key (SK2) after decrypting the TGT using its own secret key and confirming the client’s identification. The secret key of the target service is used to encrypt the ST.
- Access Request (Client to Service Server (SS)): The client transmits to the target Service Server (SS) an encrypted Service Ticket (ST) and an Authenticator (encrypted using the Client/Server Session Key).
- Mutual Authentication and Access Granted (SS to Client): The SS decrypts the ST and retrieves the Client/Server Session Key (SK2) using its own secret key. To complete the mutual authentication, the SS then transmits a confirmation message encrypted with SK2 back to the client. The user can access the service after establishing a secure session.
You can also read What is EAP-TLS Meaning, How EAP TLS Works & Advantages
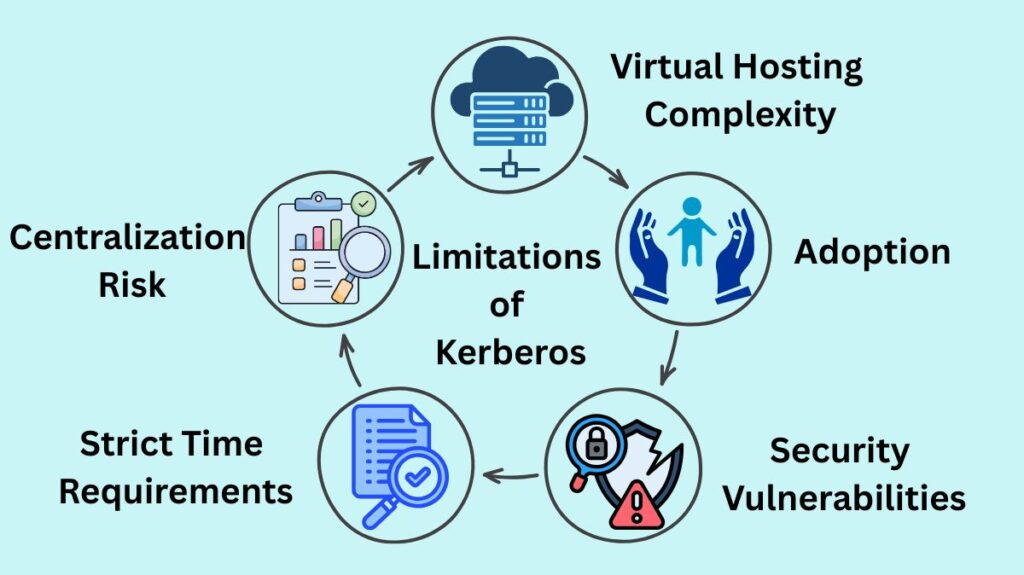
Limitations of Kerberos
An essential part of IT infrastructure is Kerberos. By default, it utilizes UDP port 88.
- Adoption: Kerberos is the default authentication mechanism in Microsoft Windows 2000 and later versions, especially when clients are connected to a Windows domain. Software supporting Kerberos authentication is also included in a number of Unix-like operating systems, such as Red Hat Enterprise Linux, Apple’s macOS, and FreeBSD.
- Security Vulnerabilities: Although Kerberos is thought to be secure because of its robust encryption, it is not perfect. There are various attack routes, including malware that degrades encryption, brute force password attempts, and forging tickets (golden or silver tickets).
- Strict Time Requirements: Because tickets have time availability limitations, all participating hosts’ clocks must be in sync within predetermined bounds, usually no more than five minutes apart.
- Centralization Risk: Since the centralized KDC controls all authentications, an attacker could pose as any user if this infrastructure is breached.
- Virtual Hosting Complexity: Clustered setups and virtual hosting are made more difficult by the fact that each network service that needs a distinct host name requires its own set of Kerberos keys.
Because of its strong ticket-based SSO functionality, Kerberos is still the back-end technology for many contemporary security solutions even though it has been around for decades.
Anology
Consider a safe airport check-in system to get an idea of how Kerberos operates. At the central desk (the AS), you just need to present your passport (your password) once to verify your identification. Rather than returning your passport, the desk gives you a tiny key (the Client/TGS Session Key) to access the security gate and an encrypted Boarding Pass (the TGT) that demonstrates the AS’s confidence in you. You no longer need to provide your passport in order to board a particular flight (the Service Server).
When you bring your boarding pass to the TGS secondary gate, they use their key to validate it. After that, they give you a specific, flight-dated Gate Ticket (also known as the Service Ticket), which is encrypted with the gate agent’s special key. When the gate agent (SS) receives your gate ticket, they use their special key to verify that you are the authorized passenger and allow you to board the aircraft. You never left the initial check-in area with your original password.
You can also read EAP and How Does Extensible Authentication Protocol Work?
