In this article, we learn about what network security is, why network security is important, and LAN threat mitigation techniques.
What Is Network Security?
In order to safeguard the confidentiality, accessibility, and integrity of computer networks, network security integrates a wide range of technologies, procedures, and equipment. Network security is necessary for organizations of all sizes, sectors, and infrastructure types to guard against the always-changing world of cyber threats.
Conventional network security uses hardware and software solutions in conjunction with rules and configurations to safeguard the network and its information. However, this approach cannot fulfill the needs of today’s sophisticated network architectures, which have a greater, more vulnerable attack surface than the classic perimeter-based network of former days.
Threat actors use cutting-edge technology, such as automation and artificial intelligence (AI)-powered botnets, to identify holes, take advantage of them, and evade discovery since they are aware of how vulnerable the current network is. Everywhere in devices, data, people, places, and applications, they search for security flaws.
You can also read What is MAC Address Aging, How it Works And Configuration
Why Network Security is Important?
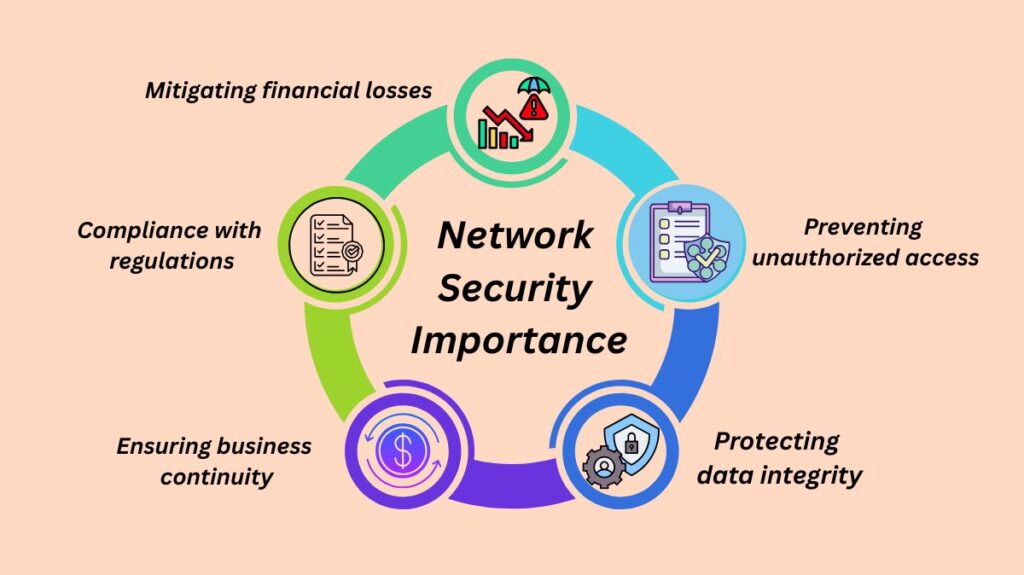
Network security is vital for protecting sensitive data and maintaining the integrity and functionality of computer networks. Without effective network security measures, firms suffer a range of hazards including data breaches, financial losses, and brand damage. Ensuring network security helps in:
Preventing unauthorized access: Network security procedures make sure that only authorized users may access vital systems and data, protecting networks from unwanted access.
Protecting data integrity: Network security protocols guard against data manipulation and guarantee the precision and dependability of data. For businesses that handle sensitive data, including financial information, private records, and intellectual property, this is especially crucial.
Ensuring business continuity: DDoS assaults and other cyberattacks have the potential to interfere with daily operations. Effective network security techniques help in limiting these risks, assuring the uninterrupted availability of services and operations.
Compliance with regulations: Strict data protection measures are required by rules in several businesses. Network security helps firms comply with regulations like GDPR, HIPAA, and PCI-DSS, avoiding legal penalties and maintaining consumer trust.
Mitigating financial losses: Data theft, ransom payments, and business interruptions can all lead to large financial losses as a result of cyber disasters. By preventing or promptly responding to accidents, network security can help lower these possible losses.
LAN threat mitigation techniques
The entire suite of security techniques, tools, and regulations used to shield a Local Area Network (LAN) from intrusion, disruption, and data theft is known as LAN Threat Mitigation. In order to keep the network safe, mitigation aims to lessen or stop common LAN security threats like flooding, spoofing, and unauthorized access.
A layered defense that combines preventive measures, detective controls, and strong response plans is the foundation of an effective threat mitigation strategy. Mitigation frequently focuses primarily on safeguarding the access layer, where endpoint devices connect to the network.
To stop a variety of attacks from being launched from end-user devices that are directly connected to access ports, Cisco switches integrate a number of specialized security capabilities. Port security, Dynamic ARP Inspection (DAI), DHCP snooping, identity-based networking, and setting up a nondefault native Virtual LAN (VLAN) are common methods for mitigating access layer threats.
The following lists the fundamental technical methods for LAN security threat mitigation, arranged according to the particular threat they target:
Access Layer Protection and Device Control
These techniques secure the connection point between end-user devices and the network switch, commonly known as the access layer.
Unauthorized Device Access and MAC Flooding
- Port Security: This technique limits a port to a certain set of MAC addresses and limits the number of MAC addresses allowed per port. It is especially made to defend the switched LAN from CAM table overflow (MAC Flooding) and MAC spoofing attacks.
- Mitigation: Limit the number of MAC addresses per port by turning on port security on switches.
- Violation Modes: The switch can switch between Shutdown (default, forcing port into an error-disabled state), Restrict (dropping traffic from unknown MACs exceeding the limit), or Protect modes in the event of a violation.
- 802.1X Authentication: 802.1X authentication restricts device access by requiring users to authenticate in before connecting to a LAN port.
- Network Access Control (NAC): All devices trying to connect to the network are subject to security policies enforced by Network Access Control (NAC) solutions. A device may be placed in quarantine or limited to a non-critical section if it fails a security check (for example, by lacking antivirus software).
ARP Spoofing / ARP Poisoning (Man-in-the-Middle)
- Dynamic ARP Inspection (DAI): DAI is a security feature that filters incoming ARP messages on untrusted ports. It is used to stop ARP spoofing (where an attacker sends fake ARP replies to redirect traffic).
- Mechanism: DAI confirms the correctness of an ARP message by comparing the origin IP and origin MAC addresses to the values contained in the DHCP Snooping binding table. DAI throws away the ARP if they don’t match.
DHCP Snooping Attacks (Rogue DHCP Server)
- DHCP Snooping: This Layer 2 security feature validates DHCP messages by acting as a firewall between untrusted hosts and trusted DHCP servers. It mitigates threats where an attacker sets up a fake DHCP server to intercept traffic.
- Mechanism: The DHCP mechanism. Switch interfaces are categorized by Snooping as either untrusted (allowing just requests, usually client connections) or trusted (allowing all DHCP messages, usually uplinks or server connections). It produces a binding table of legal DHCP flows, which is then used by DAI.
Network Segmentation and Traffic Control
These techniques isolate network sections and filter specific malicious traffic streams.
IP Spoofing
- Access Control Lists (ACLs): ACLs, or access control lists, are collections of criteria used to classify and regulate packet flow. They can filter packets, blocking external traffic that purports to be from the internal network (IP spoofing).
- Unicast Reverse Path Forwarding (uRPF): uRPF, or Unicast Reverse Path Forwarding, reduces the impact of spoof IP packets. The router looks at its routing table when a packet enters an interface; if the interface is not the most efficient way to get to the packet’s source address, it is deemed to be a spoof and is dropped.
VLAN Attacks (Hopping and Double Tagging)
By limiting the number of hosts that receive flooding frames, Virtual Local Area Networks are typically used to lower security threats. To mitigate attacks that try to breach this logical separation:
- Disable Dynamic Trunking Protocol (DTP) negotiations on non-trunking ports using the
switchport mode accesscommand. - Manually enable trunk links using
switchport mode trunkand disable DTP negotiations on trunking ports usingswitchport nonegotiate. - Set the native VLAN to a VLAN other than VLAN 1, as VLAN 1 is the default and can be exploited through attacks like double tagging.
- Disable unused ports and assign them to an unused VLAN.
Broadcast Storms and Network Loops
- Storm Control: To control and restrict excessive broadcast traffic that could overload the LAN and result in problems, this switch option should be enabled.
- Spanning Tree Protocol (STP): Broadcast storms can result from network loops, which are avoided by the Spanning Tree Protocol (STP).
- STP Guards (BPDU Guard and Root Guard): Layer 2 controls called STP Guards (BPDU Guard and Root Guard) are used to defend the infrastructure from attackers who might try to link a low-priority switch to become the root switch.
Comprehensive and Strategic Mitigation Tools
Beyond specific Layer 2 controls, organizations implement broader strategies:
Identity and Zero Trust
- Zero Trust Architecture (ZTA): This runs on the idea of “never trust, always verify,” meaning no user or device, even within the network perimeter, is trusted by default. Access is only given to those who need to know and only after verification.
- Principle of Least Privilege (PoLP): By granting users only the minimal amount of access and permissions necessary for their jobs, the Principle of Least Privilege (PoLP) reduces the possible impact of a hacked account.
- Multi-Factor Authentication (MFA): Even if credentials are stolen, imposing MFA on user accounts, particularly those with privileged access, prevents unwanted access.
Endpoint and Application Protection
- Endpoint Detection and Response (EDR)/Antivirus: By installing sophisticated Malware Protection (AMP) or EDR on every endpoint, you can identify and stop malware and sophisticated threats with automated response capabilities and ongoing monitoring.
- Regular Patching: To fix security flaws, a strong vulnerability management plan makes sure that the firmware of all network devices, operating systems, and apps is updated regularly.
- Application Visibility and Control (AVC): AVC protects against attacks that employ random port numbers by enabling in-depth examination of the application layer data to identify programs.
Monitoring and Incident Response
- Intrusion Prevention Systems (IPS): An IPS monitors traffic for unusual patterns (signatures) and can actively block or drop hostile traffic, halting an attack before it starts. IPS is particularly effective against denial-of-service (DoS) attacks.
- Security Information and Event Management (SIEM): SIEM systems gather, standardize, and examine security logs from every network device in real time, enabling security professionals to promptly identify and notify them of irregularities and possible events.
- Incident Response Plan (IRP): An organization’s recorded strategy detailing the containment, eradication, and recovery actions it will take in the event of a breach is known as an incident response plan, or IRP.
Wireless LAN (WLAN) Specific Mitigation
Although your query focuses on LAN, the sources detail specific steps for securing WLANs to prevent them from becoming conduits for threats to the wired network:
- Turn off the default SSID and pick a name that has nothing to do with the business.
- Use robust encryption, such as AES-enabled IEEE 802.11i (WPA2). The next best practice is to use WPA with TKIP.
- Use integrated Wireless Intrusion Prevention Systems (IPSs) to stop rogue access points (APs) and protect the wired network from wireless attacks.
- Use location tracking to eliminate rogue devices permanently.
You can also read Extended Access Control List And Standard Vs Extended ACL
