In this article, we learn about what is Remote Access VPN, Features, How Does Remote Access VPN Work, Types of Remote Access VPN, Advantages of Remote Access VPN, Disadvantages of Remote Access VPN, Comparison to Site-to-Site VPN and Modern Context.
What is Remote Access VPN?
One kind of virtual private network, called a Remote Access VPN (RA VPN), sometimes referred to as a Client VPN, is made to give individual users safe access to a private network, such as a business’s internal corporate network, over an unprotected public network, like the Internet.
For both residential and corporate users, this solution is ideal, especially for telecommuters, contractors, remote workers, and mobile users who must access internal resources from off-site locations, such as databases, file servers, applications, and intranets.
You can also read Components of DHCP Dynamic Host Configuration Protocol
Features
- Traffic Scope: All traffic routed to the business network is encrypted using a full client VPN (such as AnyConnect), which enables the PC to use any enterprise network application.
- Split Tunneling: Split tunneling is a feature of full-tunnel solutions (AnyConnect and IPsec remote access) that sends all other traffic straight to the Internet while rerouting communication intended for particular HQ subnetworks across the VPN tunnel. Split tunneling is seen to be less safe, despite its convenience.
- Virtual IP Address: For traffic transmitted via the tunnel, programs such as the AnyConnect SSL VPN client or IPsec VPN client give the remote user a virtual IP address. Clientless SSL VPNs are usually proxied off the ASA rather than assigning an IP address.
How Does Remote Access VPN Work
The way a Remote Access VPN operates is by creating a VPN tunnel, a secure, encrypted connection between the device of the individual user and the network perimeter of the company. Usually, this connection is transient and on-demand.
Key steps in the process include:
- Client Software: To start and maintain the tunnel, the user has to execute certain VPN client software on their device (such as a laptop or smartphone), which may be a client app or an OS feature.
- Authentication: The client makes communication with the organization’s server, concentrator, or collector, also known as the VPN gateway. Using methods like credentials, digital certificates, or Multi-Factor Authentication (MFA), the gateway verifies the user’s identity.
- Tunnel Establishment: The safe, encrypted tunnel is created after authentication.
- Data Transmission: The VPN gateway decrypts all data that is sent between the corporate network and the remote user once it has been encrypted by the client and sent across the tunnel. By preventing data from being intercepted over unreliable public Wi-Fi, this procedure guarantees secrecy and data integrity.
- Network Access: The user’s device functions as though it were physically on the private network once it is connected. For traffic sent over the tunnel, solutions such as the AnyConnect SSL VPN client may give the remote user a virtual IP address.
Types of Remote Access VPN
Several protocols are supported by remote access VPNs in order to create secure tunnels:
- TLS/SSL VPN: The Transport Layer Security (TLS) protocol, which replaced the earlier SSL protocol, is commonly used by remote access VPNs. SSL VPNs can be accessed by lightweight clients or browsers.
- IPsec VPN: This network-layer protocol suite offers robust authentication and encryption. Traditionally, IPsec remote access VPNs require client software to be installed and configured.
- Other Protocols: Other widely used protocols include L2TP (typically in conjunction with IPsec), WireGuard (modern, lightweight, and quick), and OpenVPN (renowned for its flexibility and robust security using SSL/TLS).
There are various methods for implementing remote access VPNs:
- Client-Based VPN (Full Tunnel): Needs specific client software installed, such as Cisco AnyConnect. All packets transferred from the device to the corporate network are secured using this technique. Split tunneling, which enables certain non-sensitive traffic (such as personal internet browsing) to get around the encrypted VPN tunnel, is frequently supported by full-tunnel solutions.
- Clientless VPN (Web VPN): This method does not require the installation of specialized client software; instead, it uses the TLS features that are already present in a typical web browser to establish a secure session. This technique only encrypts the data supplied during that browsing session, making it appropriate for restricted access to particular resources.
You can also read Hybrid Intrusion Detection System HyIDS For Network Security
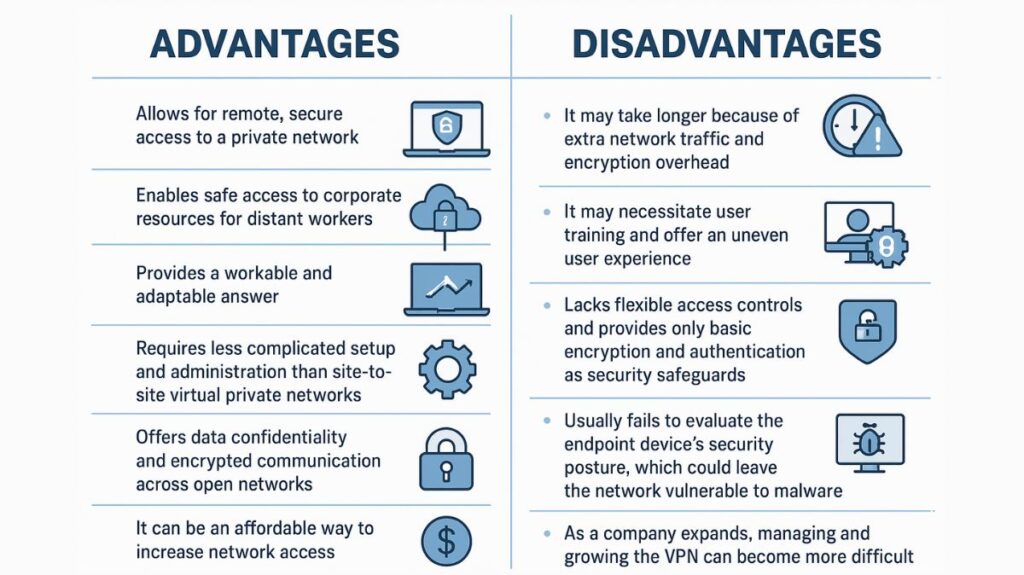
Advantages and Disadvantages of Remote Access VPN
Comparison to Site-to-Site VPN
Remote Access VPNs differ fundamentally from Site-to-Site VPNs:
| Aspect | Remote Access VPN | Site-to-Site VPN (Router-to-Router) |
|---|---|---|
| Connection Type | Connects individual users/devices (host-to-network) to a private network. | Connects entire networks (e.g., branch offices) to each other. |
| Users Allowed | Multiple users are allowed. | Multiple users are not allowed (in the context of a single tunnel definition). |
| Setup Requirement | Requires every remote access user to initiate the VPN tunnel setup. Requires VPN client installation on each device. | Does not require setup on each client device, as the gateway manages traffic. |
| Typical Use | Used by roaming users or telecommuters accessing resources securely. | Used by office LAN users in branch offices connecting to servers at headquarters. |
| Primary Protocols | Supports SSL and IPsec (often TLS, OpenVPN, WireGuard). | Typically uses IPsec security method. |
Modern Context
Although VPNs for remote access were once the industry standard for remote security, their “legacy incarnation” is starting to fall behind more competitive options. Due to their poor user experience and extensive configuration requirements, network-centric solutions like classic RA VPNs may become vulnerable as network topologies change and applications migrate to the cloud.
The following contemporary substitutes for or additions to conventional VPNs:
- Zero Trust Network Access (ZTNA): This method lowers risk by concentrating on user- and application-centric access, allowing authorized users to access only particular apps (forming secure portions of one application) rather than putting them on the entire network.
- Secure Access Service Edge (SASE): Wide area network (WAN) capabilities and strong security features are combined in the Secure Access Service Edge (SASE) framework, which is provided as a single, cloud-native service. Compared to conventional VPNs, SASE is typically thought to provide superior security and scalability.
You can also read What is HIDS Host Intrusion Detection System & HIDS vs NIDS
