Ansible CCNA

Ansible CCNA is a sophisticated, open-source IT automation tool used primarily for configuration management, application deployment, task automation, and orchestration across multiple infrastructures, including servers, cloud environments, and network devices. Infrastructure as Code (IaC), which treats infrastructure management like software development, is made possible by this set of software tools.
Originally authored by Michael DeHaan in 2012 and later acquired by Red Hat in 2015, Ansible is famous because to its simplicity and agentless architecture.
Ansible CCNA Core Architecture and Key Features
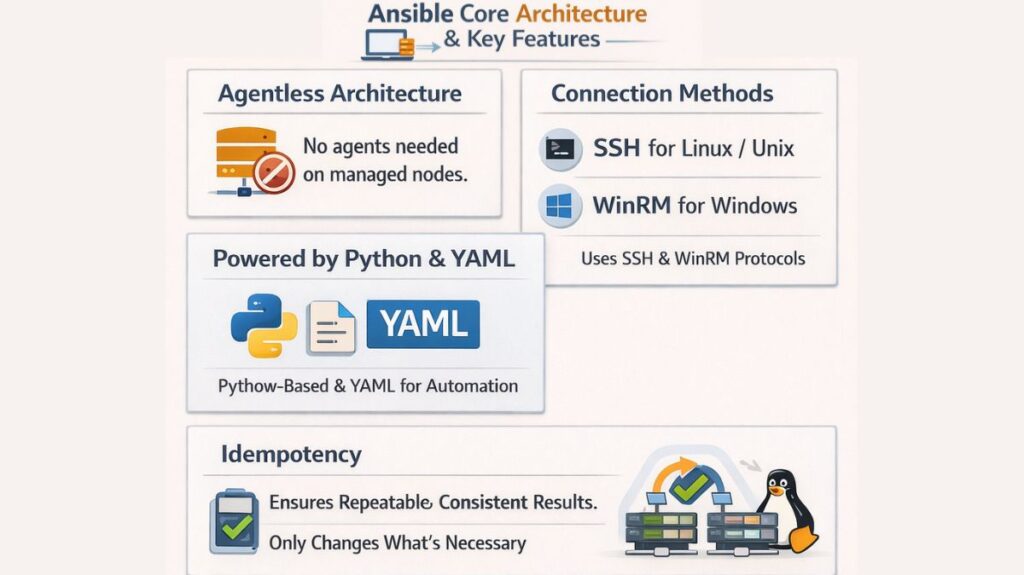
Ansible runs utilizing a simplistic, push-based architecture and relies on common protocols for communication, avoiding the need for deployed agents.
Agentless Architecture: This is a distinctive characteristic. No special agent software needs to be installed or executed on the distant servers (managed nodes).
Connection Method: Ansible interfaces with managed nodes utilizing native protocols: SSH (Secure Shell) for Linux and Unix-like systems, and WinRM (Windows Remote Management) which permits PowerShell execution, for Windows systems.
Language Base: Ansible is developed using Python. A straightforward declarative language based on YAML (Yet Another Markup Language) is used to write automation instructions.
Idempotency: Playbooks are supposed to be idempotent, meaning that they can be executed several times without generating unwanted modifications. Ansible only changes what has to be changed to attain the intended state, ensuring reliability and consistency.
You can also read What is Network Configuration Protocol & NETCONF Operations
Ansible CCNA Main Components
Ansible depends on a number of essential elements to function:
Control Node: This is the machine where Ansible is installed and from which all automation instructions and Playbooks are run. It often runs on Linux or Unix-like operating systems that support Python.
Managed Nodes (Hosts): These are the target systems (servers, network devices, cloud instances) that Ansible configures and controls.
Inventory: A file, often in INI or YAML format, that lists and groups the controlled nodes. For every host that Ansible communicates with, it operates as the one source of truth. The inventory can be sourced dynamically or from cloud-based sources.
Modules: These are short, reusable chunks of code (typically written in Python, Perl, Ruby, or Bash) that Ansible briefly pushes to the managed nodes to do specific tasks, such as installing packages (apt, yum), managing files (copy), or configuring services (service).
Playbooks: These are YAML files that define an ordered list of jobs for repeated execution. Playbooks specify the desired system state and are the heart of Ansible automation, mapping groups of hosts to a set of roles.
Tasks: The essential units of action or instruction inside a playbook, each often calling a single module.
Roles: Roles are a means to organize and reuse Ansible content, containing collections of variables, handlers, tasks, and templates to execute a specified purpose (e.g., setting up a web server).
Facts: Information about the managed nodes (such as CPU, RAM, and operating system type) that Ansible gathers automatically before running tasks.
You can also read What is RESTCONF, Architecture and RESTCONF vs NETCONF
Ansible CCNA Use Cases and Enterprise Offering
Ansible is deployed for a wide range of services, allowing teams to automate repetitive tasks and eliminate human error.
Configuration Management: Ensuring systems retain a consistent state and checking against the intended configuration to detect configuration drift.
Application Deployment: Installing software on numerous devices simultaneously.
Orchestration: Automating complex, multi-step workflows across different systems.
Network Automation: Managing multi-vendor network equipment like routers and switches, frequently utilizing SSH or NETCONF.
Provisioning: Setting up new servers and cloud instances.
The Ansible Automation Platform (AAP), a commercial product from Red Hat, offers sophisticated capabilities including job scheduling and role-based access control (RBAC), as well as a web-based interface (derived from the open-source AWX project) and a REST API for enterprise-level use. Sensitive data, such passwords or keys, can be secured with Ansible Vault, which encrypts files.
You can also read What is REST API, Benefits of REST API, and Applications
Ansible CCNA Configuration Management Capabilities
Ansible performs numerous key configuration management functions:
Configuration Provisioning: This is the key function in which Ansible implements configuration changes based on updated files in the configuration management system.
Configuration Monitoring: Ansible can evaluate a device’s actual configuration against the planned ideal configuration established in the central system (a process sometimes termed configuration monitoring or enforcement) to detect configuration drift.
Modules: Ansible employs internal modules to do specific tasks (e.g., controlling a banner or enabling BGP). These modules are normally given by the network vendor.
You can also read What is Network Configuration Management NCM & its Benefits
