This article explain about Puppet Agent In CCNA And Puppet in detail with its functions and features.
Puppet CCNA
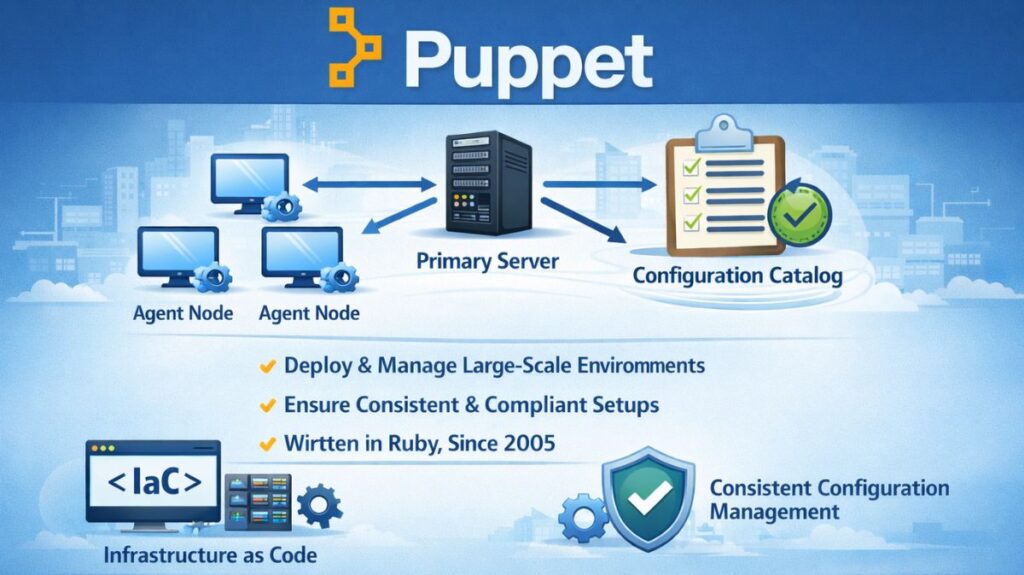
Puppet automates server infrastructure deployment, setup, and maintenance in large-scale environments using open-source software configuration management (CM) and Infrastructure as Code (IaC). It sends data from secondary devices to a primary device using client-server architecture to create configuration catalogs depending on resource states. This technique ensures consistent and effective system configuration management across numerous situations.
Developed originally in 2005, Puppet is fundamentally written in Ruby. It is well regarded for handling intricate infrastructures and is very good at enforcing uniform setups and compliance.
You can also read What is RESTCONF, Architecture and RESTCONF vs NETCONF
Architecture and Operation
Puppet uses the master-agent model, a client-server architecture.
Components:
- Puppet Server (Master): Configuration definitions, configuration compilation, and agent communication are all handled by this central server.
- Puppet Agent (Client): This program runs on all controlled machines (nodes) and enforces the configurations.
- Facter: This agent program component collects Facts about the node’s current state (e.g., operating system, IP address, kernel details).
- PuppetDB: This centralizes Puppet data, including facts, catalogs, and reports, speeding up access and providing an API for infrastructure data.
Pull Model Workflow: Puppet implements a pull approach, where the agent starts contact with the server. The typical configuration method is:
- The Puppet Agent starts periodically (typically every 30 minutes).
- The Agent uses Facter to gather Facts and communicates them safely to the Master.
- The Master uses these Facts, combined with predetermined configurations (Manifests), to construct a Catalog a resource-dependency tree specifically specifying the desired state for that agent.
- The Agent downloads the Catalog and does the necessary operations to enforce the desired configuration on the node.
- After then, the Agent provides the Master with a report that includes the configuration run’s outcomes.
- Communication between the master and agent is encrypted via SSL encryption.
Protocol Puppet often communicates with the controlled device over HTTP (REST) protocols when operating with an agent (the standard setup).
You can also read What is REST API, Benefits of REST API, and Applications
What is the Puppet Agent?
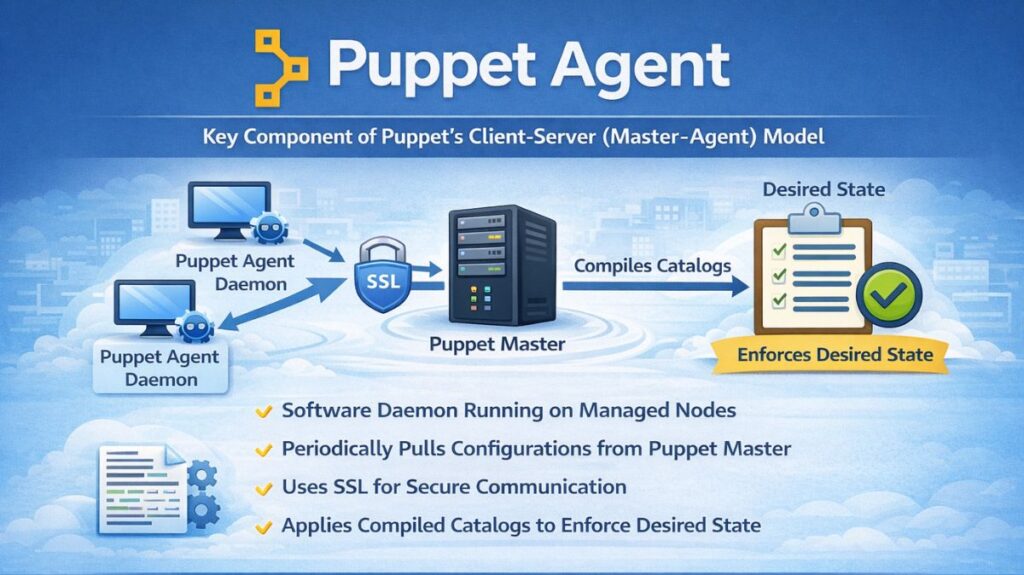
Puppet, a client-server configuration management system (master-agent model), relies on the Puppet Agent. Puppet Agent is a software daemon running on managed network nodes (servers, switches) that periodically pulls configurations from a central Puppet Master via SSL. It uses a “pull” model, enforcing the desired state on devices by applying compiled “catalogs,” making it a key declarative configuration management tool.
Role and Function
The Puppet Agent is the client program deployed on all managed hosts, or nodes, that need configuration. Its major duty is to enforce the desired configuration state on the system.
It is often run as a service or daemon on the client workstation. For configuration to occur, Puppet Agents must have particular privileges, frequently requiring root permissions on the node, to apply the configuration catalogs retrieved from the Puppet Master.
Operational Workflow (Pull Model)
Puppet implements a pull paradigm, meaning the agent begins contact with the master server to retrieve configurations. This pull procedure normally follows these steps:
- Start and Facts Collection: On the managed node, Puppet Agent starts every 30 minutes. Facter program collects node status data like hostname, IP address, operating system, and kernel. The agent delivers these details safely to the Puppet Master.
- Catalog Retrieval: The agent requests configuration instructions from the Puppet Master. The Master uses the submitted Facts and its stored configuration code (Manifests) to construct a Catalog particularly for that agent, which defines the desired state for all managed resources.
- Configuration Enforcement: The Puppet Agent downloads the Catalog and compares its current state to the catalog’s desired state. Configuration drift is corrected by the agent by restoring the node.
- Reporting: After applying or trying to apply the configuration, the agent provides run results to the Master, including modifications, successes, and failures.
Communication and Security
SSL/TLS encryption and protected certificates are used to create communication between the Puppet Agent and the Puppet Master. The agent must seek an SSL certificate from the master on its first contact to gain communication permissions. This encryption guarantees data breaches are prevented and allows mutual authentication and verification between the master and agent.
For managing network devices that may not support the installation of a native Puppet Agent, Puppet can leverage a proxy agent running on an external host to conduct the management chores.
The concept of the Puppet Agent continuously enforcing the required configuration helps to control configuration drift by automatically checking in with the master to assure compliance.
You can also read What is Network Configuration Management NCM & its Benefits
Key Concepts
Puppet relies on several basic notions to enforce system state:
Manifests and Resources: Configuration files, called Manifests (which commonly use a .pp extension), define the intended configuration state using Resources. Resources represent system components like files, packages, services, or people, and the desired settings for them.
Modules and Classes: Configurations are grouped into Modules, which are reusable collections of manifests, files, and templates specifying a system component (such configuring a web server). Modules contain Classes, which aggregate resources for machine states.
Hiera: This utility stores configuration data (e.g., hostnames, IP addresses) in a hierarchical location apart from the main configuration code.
Idempotency: Since Puppet only changes if the current state differs from the planned state, applying a configuration repeatedly guarantees the same result.
Puppet’s core languages
Puppet involves multiple basic languages for its functionality and configuration:
Puppet’s Domain-Specific Language (DSL): Puppet describes the intended final state of the system configuration using a custom declarative language. The configuration files, referred to as Manifests, employ this DSL. Users can define the resource and state without specifying how to configure it with this declarative method. Puppet declaratively configures Unix-like and Windows systems using this language. The resource syntax is identical to Ruby code.
Ruby: Ruby underpins Puppet. Puppet manifests were originally Ruby scripts with a.pp extension, but now they largely contain the DSL.
Supporting Languages
Important Puppet components are written in a number of additional languages:
C++: C++ is used to create Facter, Puppet’s cross-platform system profiling library that gathers node data.
Clojure: Both PuppetDB and Puppet Server are written in Clojure.
You can also read Ansible CCNA Architecture, Components And Key Features
Benefits and Editions
Puppet is useful for configuration management because it allows teams to specify and enforce configurations programmatically, leading to benefits like:
Configuration Drift Control: Puppet enables to automatically repair configuration drift where a device deviates from the intended state by continuous monitoring and desired state enforcement.
Consistency and Compliance: It ensures system configurations remain standardized, helping to fulfill security and compliance needs by automating standards and policies-as-code.
Cross-Platform Support: It supports Linux, Solaris, BSD, Mac OS X, AIX, HP-UX, and Windows.
Module Ecosystem: Automation efforts are accelerated by the Puppet Forge, a library of thousands of pre-built modules produced by Puppet specialists and the community.
Using an open-core paradigm, Puppet has two primary versions:
Open Source Puppet (Puppet Core): The free-software version. This is a rudimentary version of the Puppet configuration management tool. It may be obtained from Puppet’s website and is licensed under the Apache 2.0 system.
Puppet Enterprise (PE): A patented, premium IT Operations Platform with a GUI, orchestration, RBAC, and comprehensive reporting for scaled infrastructure management.
When to avoid Puppet?
Small-scale projects: Puppet is too complicated for small infrastructure or single-computer management.
Frequent configuration changes: Puppet’s automation may be inconvenient for projects that require regular configuration changes.
Steep learning curve: It may overwhelm the upsides of lesser jobs for teams untrained with Puppet.
Real-time updates: If immediate updates are required, Puppet’s time-based paradigm might not be compatible.
You can also read CCNA Chef Architecture, Advantages And Disadvantages
Click here to know about the IP & Network Tools Calculators
