Rogue AP Detection
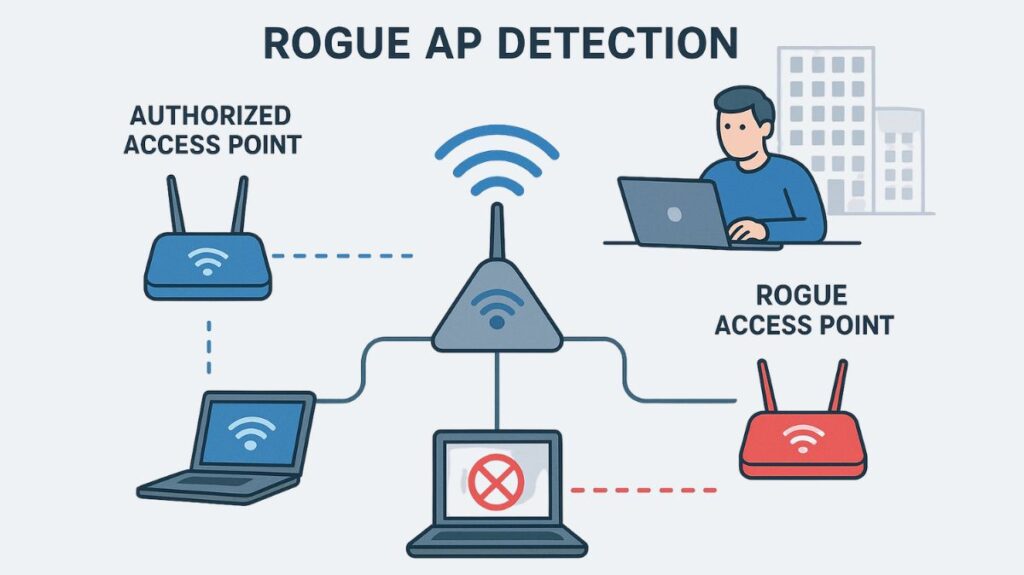
A security function called “rogue AP detection” finds unauthorized wireless access points (APs) on a network. It operates by looking for APs that aren’t on the trusted list. It can do this in several ways, like keeping an eye out for beacon signals on unapproved channels or comparing signals from the air with the wired network. Following detection, the system can be set up to notify administrators or initiate automatic actions, such as disconnecting clients from the rogue AP by sending de-authentication frames.
Any device that shares your radio frequency (RF) spectrum but is not under your control, often circumventing security measures, is considered a rogue access point (AP). Rogues become especially harmful when they are found on a wired network, which gives unauthorized users an easy back door, or when they use the same Service Set Identifier (SSID) as the legal network (honeypot assault).
The three primary stages of the Cisco Unified Wireless Network (UWN) solution detection, classification/identification, and mitigation are used to control rogue devices.
You can also read Console Port Cisco Switch Configuration: Step-by-Step Guide
Rogue Detection
To find rogue devices, detection employs a Radio Resource Management (RRM) scan. Determining whether an AP is unauthorized and, consequently, whether it is connected to the secured wired network is the aim of detection.
In order to find visible Wi-Fi signals (SSIDs, MAC addresses, and BSSIDs), managed access points (APs) or specialized sensors continuously search the radio frequency spectrum. Any AP that isn’t on the approved (or “known good”) list is marked as possibly dangerous. The rogue AP MAC address, RSSI, SNR, channel, security policy, and SSID (if broadcast) are among the detected rogue details that the controller has collected.
The Cisco UWN uses two primary methods for scanning:
- Off-Channel Scan
- Local Mode and Flex-Connect (in connected mode) APs are responsible for this.
- It makes use of a time-slicing technology that enables channel scanning and client service to happen at the same time.
- By default, the AP goes off-channel for 50 milliseconds every 16 seconds. This restricts the impact on performance to a maximum of 1.5%.
- The extended detection times (3 to 60 minutes) are caused by the division of cycles between scanning and client service.
- Monitor Mode Scan
- Adaptive wIPS monitor mode APs and monitor mode APs do this.
- This mode scans every channel in every frequency band using all of the radio time.
- They are better at identifying bursty traffic, such as rogue clients, because their specialized scanning enables faster detection and more thorough data collecting.
- Local mode APs listen for 50 ms on each channel, while monitor mode APs listen for 1.2 ms.
Rogue Identification and Classification
The following step after detecting a rogue over the air is to determine its connection status and degree of risk. Detected rogues are unclassified by default.
Rogue Identification (Wired Network Correlation)
If the rogue device is linked to the company’s wired network, it can be identified using a variety of techniques, which greatly increases the threat level:
- Rogue Detector APs
- These APs correlate ARP information from the wired network with rogue information heard over the air (only Wave 1 APs can be configured in this manner).
- A MAC address is marked as “on the wired network,” and its alarm severity is increased to critical if it is detected both wirelessly (as a rogue AP/client) and on the wired network.
- Rogue Location Discovery Protocol (RLDP)
- Verifying if a particular rogue AP is linked to the wired infrastructure is the goal of RLDP.
- The nearest managed AP connects to the rogue as a WLAN client as part of the algorithm.
- Through DHCP, the managed AP tries to get an IP address from the rogue network. If it is successful, the Wireless LAN Controller (WLC) receives a UDP packet with the RLDP data. The rogue is classified as “on-wire” with a critical severity if the WLC gets this packet.
- RLDP requires DHCP availability on the rogue network and that the rogue AP be open (no encryption or authentication).
- Switch Port Traces (SPT)
- SPT, which was inspired by Cisco Prime Infrastructure (PI), tracks a rogue down to a particular port by using CDP and SNMP data on Cisco switches.
- To determine the rogue’s precise location, the PI looks through the switch’s CAM database for a match (exact MAC, +1/-1 MAC, rogue client MACs, or OUI vendor match).
Rogue Classification
Conditions that designate a rogue as either friendly or malevolent are defined by Rogue Classification Rules. Based on parameters like RSSI, SSID, security type, and client count, these rules are implemented to the controller.
Rogues can be tracked and classified in the WLC interface as follows:
- Friendly APs: Rogues that an administrator has manually designated as friendly.
- Malicious APs: RLDP or Rogue Detector APs are used to identify malicious APs.
- Unclassified APs: The default state for recently found rogues is unclassified APs.
- Custom APs: Rogue Rules are used to categorize custom APs.
You can also read Cisco Hot Standby Router Protocol HSRP Configuration, States
Rogue Mitigation
Finding the rogue’s actual position and eliminating the threat are two aspects of mitigation.
Rogue Containment (Wireless Mitigation)
A temporary technique called containment interrupts a rogue device’s service via over-the-air transmissions.
- Mechanism: In order to force related clients to disconnect, containment spoofs de-authentication packets using the source address of the rogue AP.
- Deployment: One to four managed APs can handle containment. Monitor mode APs can have up to six rogue devices per radio, but local mode/Flex-Connect APs can only have three.
- Caveats: This procedure can cause a 20% decrease in the performance of valid data and voice customers. Containment has serious legal ramifications and liabilities because it may interfere with neighboring networks, especially when it is enabled automatically.
Auto-Containment
Although it is not enabled by default, the WLC or PI can be set up to initiate confinement automatically in high-threat situations. Among the auto-containment policies are:
- Rogue on Wire: If it has been verified that the rogue is connected to the wired network.
- Use of our SSID: If the rogue is using a honey-pot assault to mimic the corporate network’s SSID.
- Valid client on Rogue AP: If the rogue is linked to a trusted client (such as one listed in the Radius/AAA server). Only the client is the target of containment.
- AdHoc Rogue AP: If an ad hoc network is identified.
Switch Port Shutdown (Wired Mitigation)
The administrator can instantly contain the threat by manually using Cisco PI to stop (shut down) the specific wired port of a rogue AP if a switch port trace is successful in identifying it. After the rogue has been physically removed, the administrator can thereafter enable the port.
Configuration and Tools
Cisco Wireless LAN Controllers (WLCs) and Cisco Prime Infrastructure (PI) are the main tools used to configure rogue detection and management.
- Rogue Records: While PI logs event history, including rogues that are no longer visible, the WLC database contains the current list of detected rogues.
- Rogue Timeout: While rogues in Friendly or Contained states continue to exist, unclassified rogues age out after a user-configurable timeout (1200 seconds by default).
- Scalability: Each controller has a different maximum database size for rogues; for instance, the 5520 and 8540 can support up to 24,000 rogue APs, while the 3504 can support up to 600. Up to 500 rogues can be found with a single rogue detector AP.
- SNMP Traps: For archival purposes, rogue events can be exported to a Network Management System (NMS) using SNMP traps.
You can also read What is Challenge Handshake Authentication Protocol CHAP
